The U.S. Department of Labor has developed an automated occupational information database, O*NET, that identifies and describes work content, work skills, and training requirements for all jobs across the country in all sectors of the economy. Much of the occupational information contained in this report is derived directly from the O*NET database, and supplemented with information from the Bureau of Labor Statistics, Census Bureau, and Labor Market and Career Information.

| Industry | % of Information Security Analysts employed | Annual Growth Rate |
|---|---|---|
| Computer systems design and related services | 24.9 | 3.94 |
| Management, scientific, and technical consulting services | 6 | 2.84 |
| Insurance carriers | 4.6 | 2.41 |
| Accounting, tax preparation, bookkeeping, and payroll services | 4.1 | 1.99 |
| Scientific research and development services | 4.1 | 2.35 |
| Employment services | 3.4 | 1.93 |
| Architectural, engineering, and related services | 3.1 | 2.26 |
| Colleges, universities, and professional schools | 2.3 | 2.15 |
| Software publishers | 2.1 | 2.92 |
| 2023 Statewide average hourly wage | $57.44 |
| 2023 National average hourly wage | $59.97 |
| 2022 National employment | 168,900 |
| 2022 Texas employment | 14,621 |
| Texas projected employment by 2032 | 21,622 |
| Texas projected annual employment and Turnover openings through 2032 | 1,760 |
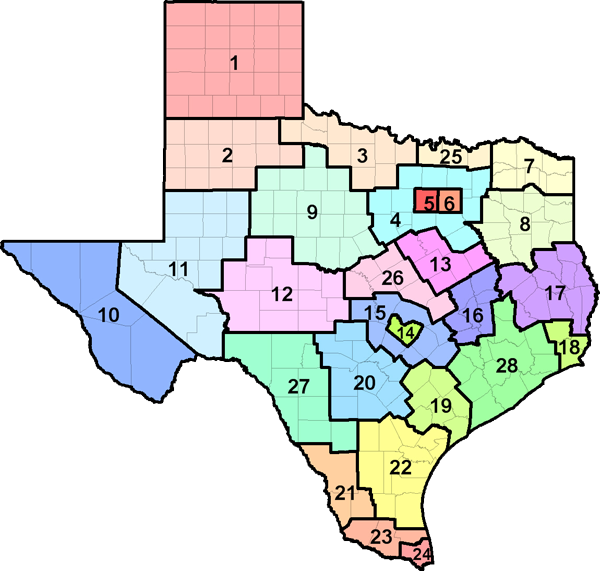
| Region | Employment | Projected Employment 2032 | Projected Annual Openings 2032 |
Annual Growth Rate |
Average Income |
|---|---|---|---|---|---|
| Texas (all regions) | 14,621 | 21,622 | 1,760 | 3.99% | $119,483.00 |
| Top 10 Relevant Knowledge Areas | Relevant Importance Levels |
|---|---|
| Computers and Electronics Knowledge of circuit boards, processors, chips, electronic equipment, and computer hardware and software, including applications and programming. |
|
| English Language Knowledge of the structure and content of the English language including the meaning and spelling of words, rules of composition, and grammar. |
|
| Administration and Management Knowledge of business and management principles involved in strategic planning, resource allocation, human resources modeling, leadership technique, production methods, and coordination of people and resources. |
|
| Engineering and Technology Knowledge of the practical application of engineering science and technology. This includes applying principles, techniques, procedures, and equipment to the design and production of various goods and services. |
|
| Telecommunications Knowledge of transmission, broadcasting, switching, control, and operation of telecommunications systems. |
|
| Customer and Personal Service Knowledge of principles and processes for providing customer and personal services. This includes customer needs assessment, meeting quality standards for services, and evaluation of customer satisfaction. |
|
| Public Safety and Security Knowledge of relevant equipment, policies, procedures, and strategies to promote effective local, state, or national security operations for the protection of people, data, property, and institutions. |
|
| Education and Training Knowledge of principles and methods for curriculum and training design, teaching and instruction for individuals and groups, and the measurement of training effects. |
|
| Mathematics Knowledge of arithmetic, algebra, geometry, calculus, statistics, and their applications. |
|
| Communications and Media Knowledge of media production, communication, and dissemination techniques and methods. This includes alternative ways to inform and entertain via written, oral, and visual media. |
| Top 10 Relevant Skill Areas | Relevant Importance Levels |
|---|---|
| Reading Comprehension Understanding written sentences and paragraphs in work-related documents. |
|
| Critical Thinking Using logic and reasoning to identify the strengths and weaknesses of alternative solutions, conclusions, or approaches to problems. |
|
| Active Listening Giving full attention to what other people are saying, taking time to understand the points being made, asking questions as appropriate, and not interrupting at inappropriate times. |
|
| Complex Problem Solving Identifying complex problems and reviewing related information to develop and evaluate options and implement solutions. |
|
| Speaking Talking to others to convey information effectively. |
|
| Writing Communicating effectively in writing as appropriate for the needs of the audience. |
|
| Monitoring Monitoring/Assessing performance of yourself, other individuals, or organizations to make improvements or take corrective action. |
|
| Judgment and Decision Making Considering the relative costs and benefits of potential actions to choose the most appropriate one. |
|
| Systems Analysis Determining how a system should work and how changes in conditions, operations, and the environment will affect outcomes. |
|
| Active Learning Understanding the implications of new information for both current and future problem-solving and decision-making. |
| Top 10 Relevant Abilities | Relevant Importance Levels |
|---|---|
| Problem Sensitivity The ability to tell when something is wrong or is likely to go wrong. It does not involve solving the problem, only recognizing that there is a problem. |
|
| Deductive Reasoning The ability to apply general rules to specific problems to produce answers that make sense. |
|
| Inductive Reasoning The ability to combine pieces of information to form general rules or conclusions (includes finding a relationship among seemingly unrelated events). |
|
| Oral Comprehension The ability to listen to and understand information and ideas presented through spoken words and sentences. |
|
| Written Comprehension The ability to read and understand information and ideas presented in writing. |
|
| Written Expression The ability to communicate information and ideas in writing so others will understand. |
|
| Information Ordering The ability to arrange things or actions in a certain order or pattern according to a specific rule or set of rules (e.g., patterns of numbers, letters, words, pictures, mathematical operations). |
|
| Oral Expression The ability to communicate information and ideas in speaking so others will understand. |
|
| Near Vision The ability to see details at close range (within a few feet of the observer). |
|
| Category Flexibility The ability to generate or use different sets of rules for combining or grouping things in different ways. |